Using Reverse SSH to Communicate with an Isolated LAN
Using Reverse SSH to Communicate with an Isolated LAN
The Secure Shell Protocol (or SSH,) provides network support personnel with a reliable, effective tool for communicating with networked devices that are otherwise inaccessible. Since Secure Shell includes powerful encryption capabilities, SSH serves as an ideal solution for communicating with devices protected by firewalls without compromising network security or running the risk that packets sent to and from secure sites might be intercepted and read via packet analysis.
SSH was originally created in response to concerns regarding the security of the older Telnet protocol, where data is transmitted as plain text. Although Telnet is still employed in many applications where security is not a concern, Telnet lacks encryption capabilities, making it unsuitable for communication via unsecured networks and the internet. SSH solves this problem using public key cryptology to verify the identity of remote users and to insure that passwords and other confidential information in transmitted packets are safe from unauthorized access.
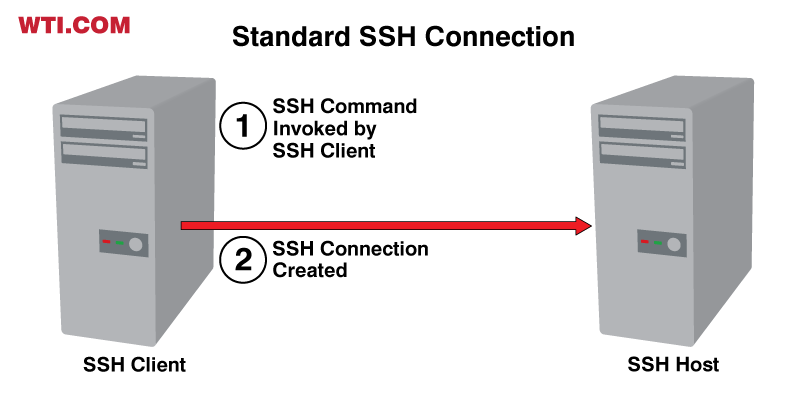
In its most basic form, SSH simply provides a secure means to communicate with an SSH server via the internet and other unsecured networks. In this case, an SSH client typically invokes an SSH command to establish a secure connection with an SSH host at a known IP address or URL as shown in the figure below. Once a connection of this sort is established, communication between the client and host is encrypted and secure.
In addition to the basic SSH connection described above, SSH also allows users to create Reverse SSH connections (also known as Outbound SSH connections,) where an SSH client sends a command to an SSH host and the SSH host then in turn establishes another connection to another device at an IP Address or URL indicated in the SSH command line as shown in the figure below.
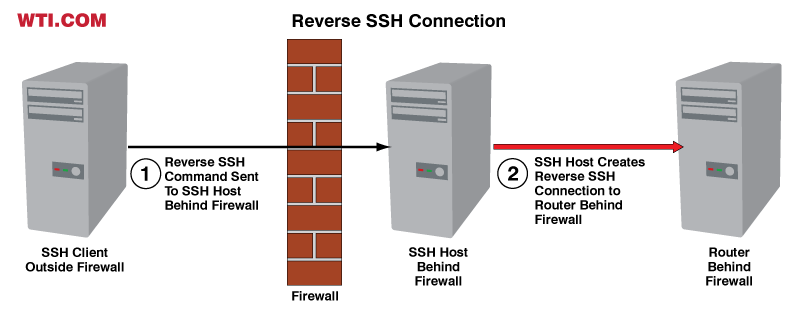
Reverse SSH connections can perform many useful roles in network management applications. In some cases the reverse SSH connection is used to provide access to networked elements located behind a firewall as shown in the example above. Providing that the firewall accepts inbound SSH connections, this allows a remote manager to establish a secure connection to devices that would otherwise be inaccessible due to the presence of the firewall.
In other cases, a reverse SSH command can be used to establish an encrypted tunnel. Encrypted tunneling is often used in cases where a firewall does not allow inbound SSH connections. In this type of application, a host behind a firewall first establishes a persistent SSH connection to a client outside of the firewall. Once this outbound SSH connection is established, the client outside the firewall can then employ a reverse SSH command to connect to the host inside the firewall via the encrypted tunnel. This effectively provides secure, two-way communication with the protected host in spite of the fact that the firewall is configured to block inbound SSH connections.
Persistent SSH connections are useful in a number of different applications because they are not limited by time constraints; if the connection times out and is terminated by the firewall, the persistent connection will be automatically restored allowing reliable communication without having to deal with constant timeouts.
Reverse SSH in Remote Network Management Applications
The encryption and authentication capabilities discussed above help to make Reverse SSH an ideal tool for managing remote devices in network applications. Due to the secure nature of Secure Shell protocol, most commercial firewalls are configured to accept inbound SSH connections and in rare cases where firewalls don’t allow inbound SSH connections, the encrypted tunneling capabilities provided by reverse or outbound SSH connections also provide a way to get around firewalls that don’t accept inbound connections.
In order to provide a comparatively simple, centralized solution for remote network management, WTI’s DSM Series Dual GigE Console Servers provide full support for SSH communication as well as access to console port command functions for connected devices. The combination of reverse/outbound SSH capabilities and remote console access allows tech support personnel to communicate with distant network elements via both Ethernet and console port connection, providing a comprehensive picture of conditions, problems and events at inaccessible network installations.
When the DSM Series Console Server includes an internal modem, dial-up communication allows communication with remote LANs in situations where normal network communication is unavailable. This means that even during WAN outages, NOC personnel can still communicate with remote network elements by dialing into the DSM and then creating a reverse SSH connection to the secure LAN at the remote site.
In addition to the remote console access capabilities made possible by traditional console servers, the SSH Hosting functions found on DSM Series Console Servers also provide support personnel with the following capabilities:
- Access to Remote Devices via both Ethernet and Console Port
- Access to More Devices than are Allowed by the Number of Serial Ports on the Console Server
- Reliable Communication when Normal Network Access is not Available
- Perfect Management Solution for Devices on an Isolated LAN
Application Examples
The following examples describe two typical applications where the reverse SSH capabilities of the DSM Series Console Server are used to provide remote access to networked devices at distant network equipment sites.
Application Example: Using a Reverse SSH Connection to Communicate with an Isolated LAN
Challenge:
Network support personnel need a secure, reliable solution for communicating with devices located on a remote LAN. The LAN at the remote site is not directly accessible via network, as is often the case in applications that are situated in locations where network access is not practical and in applications where WAN access could constitute a security risk. Since the application in this example lacks direct network access, a dial-up connection is used to provide out-of-band access to devices at the site
Solution:
A DSM Series Console Server with an internal modem is deployed at the remote site. When an administrator or technician needs access to a device at the site, a dial-up connection is first established with a WTI DSM Series Console Server at the site. Since the DSM Console Server also functions as an SSH Host and the DSM is connected to the secure LAN at the site, remote support personnel are able to employ the DSM to establish a reverse SSH connection with any device on the LAN.
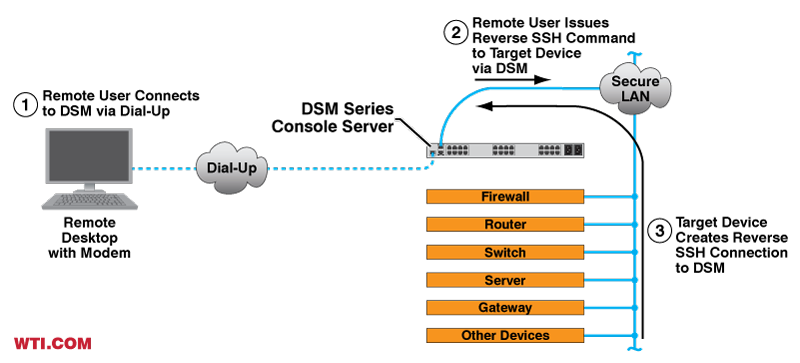
Results:
This provides administrators and support personnel with remote access to networked devices at the remote site even though direct network access is not available, allowing communication with any device connected to the secure LAN at the remote site. If desired, the serial ports on the DSM Series Console Server can also be connected to console ports on devices at the site to provide remote access to console port command functions.
In addition to allowing access to remote devices by both Secure LAN and console port via dial-up, the DSM Series Console Server can also be used to monitor conditions and events at the site. When high rack temperatures, power supply irregularities, LAN outages, unresponsive devices and other potentially troublesome conditions are detected, the DSM can create an event log to provide support personnel with a time-stamped record of events at the site.
Application Example: Using a Reverse SSH Connection for Out-of-Band Access
Challenge:In order to simplify the process of dealing with problems at a remote network equipment installation, support personnel need access to remote devices via both Ethernet and console port. In the event that normal network communication with the site is down, technicians also need a secondary out-of-band solution for communication with the site in order to remedy network outages without the need to travel to the site in person.
Solution:
A DSM Series Console Server is installed at the remote site and connected to the site’s secure LAN and a phone line. In order to provide remote access to console port command functions on devices at the site, the DSM is also connected to console ports on critical devices at the site. When WAN access to the site is up, remote personnel can establish an Ethernet connection to the DSM and then use the DSM’s SSH Hosting capabilities to create an Ethernet connection to each device at the site via Reverse SSH. In addition, remote personnel can also access console port command functions on any device at the site that is connected to a DSM serial port.
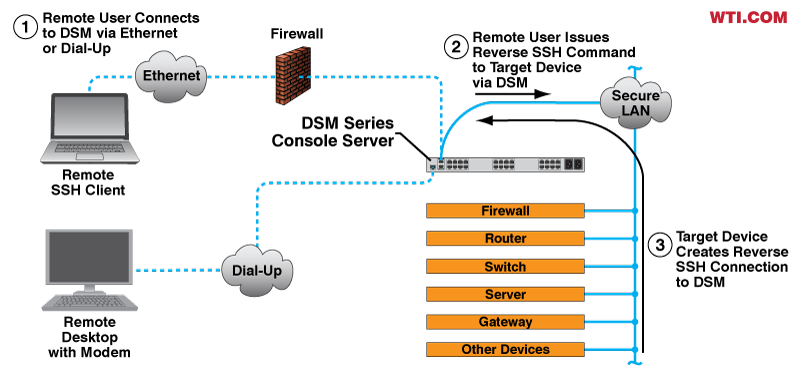
In the event that outside network access to the secure LAN at the site is down, remote support personnel can dial into the DSM and then access each device via Ethernet or console as described in the previous paragraph. When the outside network access is disrupted by a malfunctioning router or switch at the remote site, support personnel can correct the problem and restore outside network access without the need to travel to the site to deal with the problem in person.
In cases where additional out-of-band communication options are required, a DSM-E Series Dual GigE Console Server can be used in place of a standard DSM Console Server. Since DSM-E Series Dual GigE Console Servers include dual Ethernet ports, this allows technicians and support personnel to access the site via both primary/production network and secondary/maintenance network, or if desired, via both primary network plus 3G/4G/LTE cellular broadband or satellite modem.
Results:
This provides a number of different options for communication with the remote site. Support personnel can connect to the DSM Console Server via either Ethernet or Dial-up and once connected, can then communicate with network elements at the site via either reverse SSH or console port. The DSM’s SSH Hosting functionality allows direct network communication with more devices than are allowed by the number of ports on the DSM console server.
If desired, remote administrators can also employ the DSM Console Dual GigE Server’s Reverse SSH capabilities to establish an encrypted tunnel that bypasses the site’s firewall, essentially creating a secure VPN that can be used to communicate with routers, switches and other network elements.
In order to keep track of noteworthy conditions and events at the remote site, the DSM Console Server’s monitoring and alarm functions can be used to detect unresponsive devices, high rack temperatures, power supply irregularities and other potential signs of trouble. When rack temperatures, ping response or other monitored conditions exceed user-defined trigger levels, the DSM can provide immediate notification via email, text message or SNMP Trap, allowing prompt response to minor problems before they have the chance to grow into major emergencies. When suspect conditions are detected at the site, the DSM can also create a log that records the details of each event plus all user activity at the site.
Summary
A console server that supports reverse, outbound SSH connections can provide technical support personnel with a secure, versatile tool for communicating with devices at remote sites that would otherwise be inaccessible. In addition to providing access to console port command functions like other console servers, a console server with SSH Hosting capabilities also allows technicians to communicate with remote devices on secure LANs via network when outside network access is down or impractical.
In addition to providing access to devices at remote sites via both Ethernet and console port, technicians can also communicate with the remote site via both dial-up and network connection. Working together, these features simplify the process of communicating with individual devices at the site for routine communication and maintenance needs and also enable NOC personnel to deal with network outages and other problems at network equipment installations without the hassles and expenses of physical service calls or truck rolls.
Request a free demo
WTI products can be demo'd through any of the following options: